Phishing prevention has become essential as more criminals turn towards online scams to steal your personal information. We’ve learned to dodge spam emails, but phishing emails can look deceivingly credible. You will likely be exposed to a phishing attack so you’ll need to know the red flags. Because scams are nothing new on the web, but phishing is harder to spot than you might think.
Across the web, phishing attacks have baited unsuspecting victims into handing over bank info, social security numbers, and more. Plus, cybercriminals have become even savvier with their disguises. Sometimes these scams hide behind voices you know and trust, like your coworkers, your bank, or even your government. If you so much as click a link, you could be the scammer’s next victim.
What is Phishing?
Phishing persuades you to take any action which gives a scammer access to your device, accounts, or personal information. By pretending to be a person or organization you trust, they can more easily infect you with malware or steal your credit card information.
In other words, these social engineering schemes “bait” you with trust to get your valuable information. This could be anything from a social media log in, to your entire identity via your social security number.
These schemes may urge you to open an attachment, follow a link, fill out a form, or reply with personal info. By that logic, you must be on guard at all times which can be exhausting.
The most common scenario is as follows:
- You open your email and suddenly an alert from your bank appears in your inbox. When you click the link in the email, you are taken to a webpage that looks, more or less, like your bank.
- Here is the catch: this site is actually designed to steal your information. The alert will say there is a problem with your account and ask you to confirm your login and password.
- After entering your credentials on the page that appears, you are usually sent to the actual institution to enter your information a second time. By steering you to the legitimate institution, you don’t immediately realize your information was stolen.
These threats can get very elaborate and show up all types of communication, even phone calls. The danger of phishing is that it can deceive anyone that isn’t skeptical of smaller details.
To help you guard yourself without becoming paranoid, let’s unpack how phishing attacks work.
How does Phishing work?
Anyone who uses the internet or phones can be a target for phishing scammers.
Phishing scams normally try to:
- Infect your device with malware
- Steal your private credentials to get your money or identity
- Obtain control of your online accounts
- Convince you to willingly send money or valuables
Sometimes these threats don’t stop with just you. If a hacker gets into your email, contact list, or social media, they can spam people you know with phishing messages seemingly from you.
Trust and urgency are what makes phishing so deceiving and dangerous. If the criminal can convince you to trust them and to take action before thinking — you’re an easy target.
Who is at risk of Phishing attacks?
Phishing can affect anyone of any age, whether in their personal life or in the workplace.
Everyone from the elderly to young children are using internet devices nowadays. If a scammer can find your contact information publicly, they can add it to their phishing target list.
Your phone number, email address, online messaging IDs, and social media accounts are harder to hide nowadays. So, there’s a good chance that just having one of these makes you a target. Plus, phishing attacks can be broad or highly targeted in the people they choose to trick.
Spam Phishing
Spam phishing is a broad net being thrown to catch any unsuspecting person. Most phishing attacks fall into this category.
To explain, spam is the electronic equivalent of the ‘junk mail’ that arrives on your doormat or in your postbox. However, spam is more than just annoying. It can be dangerous, especially if it’s part of a phishing scam.
Phishing spam messages are sent out in mass quantities by spammers and cybercriminals that are looking to do one or more of the following:
- Make money from the small percentage of recipients that respond to the message.
- Run phishing scams – in order to obtain passwords, credit card numbers, bank account details and more.
- Spread malicious code onto recipients’ computers.
Spam phishing is one of the more popular means that scammers get your info. However, some attacks are more targeted than others.
Targeted Phishing
Targeted phishing attacks usually refer to spear-phishing or its most common variant, whaling.
Whaling takes on high-level targets, while spear phishing widens the net. Targets usually are employees of specific companies or government organizations. However, these scams can easily be aimed at anyone seen as particularly valuable or vulnerable.
You might be targeted as a customer of a targeted bank, or an employee of a healthcare facility. Even if you’re just responsive to a strange social media friend request, you might be phished.
Phishers are much more patient with these schemes. These personalized scams take time to craft, either potentially for a reward or to increase the chances of success.
Building these attacks may involve gathering details about you or an organization you happen to be involved with.
Phishers might take this information from:
- Social media profiles
- Existing data breaches
- Other publicly discoverable info
Moving in for an actual attack might be swift with an immediate attempt to encourage you to take an action. Others might build a connection with you for months to earn your trust before the big “ask.”
These attacks aren’t limited to direct messages or calls — legitimate websites might be hacked directly for a phisher’s benefit. If you’re not careful, you might be phished just by logging in to site that is normally perfectly safe.
Unfortunately, it seems many people are convenient targets for these criminals. Phishing has become a new “normal” as these attacks have ramped up in frequency.

What types of Phishing Scams should I know about?
The first hurdle is understanding what to expect from phishing. It can be delivered in all kinds of means, including phone calls, texts, and even in hijacked URLs on perfectly legitimate websites.
Phishing is much easier to understand once you’ve seen it in action. You’ve probably already seen a few of these scams and just chucked them aside as spam.
Regardless of how they are targeted, phishing attacks take many roads to get to you and most people are likely to experience at least one of these forms of phishing:
- Phishing email appears in your email inbox — usually with a request to follow a link, send a payment, reply with private info, or open an attachment. The sender’s email might be tailored to closely resemble a valid one and may contain info that feels personal to you.
- Domain spoofing is a popular way an email phisher might mimic valid email addresses. These scams take a real company’s domain (ex: @america.com) and modify it. You might engage with an address like “@arneria.com” and fall victim to the scheme.
- Voice phishing (vishing) scammers call you and impersonate a valid person or company to deceive you. They might redirect you from an automated message and mask their phone number. Vishers will try to keep you on the phone and urge you to take action.
- SMS phishing (smishing) similarly to vishing, this scheme will imitate a valid organization, using urgency in a short text message to fool you. In the message, you’ll usually find a link or a phone number they want you to use. Mobile messaging services are also at risk of this.
- Social media phishing involves criminals using posts or direct messages to persuade you into a trap. Some are blatant like free giveaways or sketchy “official” organization pages with an urgent request. Others might impersonate your friends or build a relationship with you long-term before ‘attacking’ to seal the deal.
- Clone phishing duplicates a real message that was sent previously, with legitimate attachments and links replaced with malicious ones. This appears in email but may also show up in other means like fake social media accounts and text messages.
In other cases, legitimate websites might be manipulated or imitated via:
- Watering hole phishing targets popular sites that many people visit. An attack like this might try to exploit weaknesses in a site for any number of other phishing attacks. Delivering malware, link redirection, and other means are common in these schemes.
- Pharming (DNS cache poisoning) uses malware or an onsite vulnerability to reroute traffic from safe websites to phishing sites. Manually typing a URL will still lead visitors to the malicious site if it is a victim of pharming.
- Typosquatting (URL hijacking) tries to catch people who type an incorrect website URL. For example, a website might be created that is one letter off from a valid one. Typing “Walmart” instead of “Walmart” could potentially lead you to a malicious site.
- Clickjacking uses a website’s vulnerabilities to insert hidden capture boxes. These will grab user login credentials and anything else you might enter on the otherwise safe site.
- Tabnabbing happens when an unattended fraudulent page reloads into an imitation of a valid site login. When you return to it, you might believe it to be real and unknowingly hand over access to your account.
- HTTPS phishing gives a malicious website the illusion of security with the classic “padlock next to the URL bar” indicator. While this encryption sign used to be exclusive to sites that were verified as safe, now any site can get this. So, your connection and info you send may be blocked to outsiders, but you’re already connected to a criminal.
Even your actual internet connection can be compromised by:
- Evil twin attacks mimic official public Wi-Fi at locations like coffee shops and airports. This is done in efforts to get you to connect and eavesdrop on all your online activity.
Finally, here are some more types of phishing you should be aware of:
- Search engine results phishing uses methods to get a fraudulent webpage to appear in search results before a legitimate one. It is also known as SEO phishing or SEM phishing. If you don’t look carefully, you may click the malicious page instead of the real one.
- Angler phishing impersonates a customer service representative for a real company to trick you out of information. On social media, a fake help account spots your “@mentions” to company’s social handle to respond with a fake support message.
- BEC (business email compromise) involves various means of breaching a company’s communications circle to get high-value info. This can include CEO impersonation or pretending a vendor with a fake invoice to initiate activities like wire transfers.
- Cryptocurrency phishing targets those with cryptocurrency wallets. Instead of using long-term means to mine cryptocurrency themselves, these criminals try to steal from those that already have these funds.
The truth is the list of types of phishing attacks is extensive and constantly expanding. These are some of the most common currently, but you might see new ones even in a few months.
Since these scams rapidly change to fit current events, they’ve been hard to spot. But there are ways you can keep yourself safer and being aware of the latest scams is an easy way to start.
Some examples of common phishing scams
Whilst it would be impractical and impossible to list every known phishing scam here, there are some more common ones you should definitely look out for:
Iran Cyberattack phishing scams use an illegitimate Microsoft email, prompting a login to restore your data in attempts to steal your Microsoft credentials. Scammers use your fear of being locked out of Windows and the relevance of a current news story to make it believable.
Office 365 deletion alerts are yet another Microsoft-related scam used to get your credentials. This email scam claims that a high volume of files have been deleted from your account. They give a link for you to login, of course resulting in your account being compromised.
Notice from bank. This scam tricks you with a fake account notification. These emails normally give you a convenient link which leads to a web form, asking for your bank details “for verification purposes.” Do not give them your details. Instead, give your bank a call as they may want to take action on the malicious email.
Email from a ‘friend’. This scam takes the form of a known friend who is in a foreign country and needs your help. This ‘help’ normally involves sending money to them. So, before you send your ‘friend’ money, give them a call first to verify whether it’s true or not.
Contest winner/Inheritance email. If you’ve won something unexpectedly or received an inheritance from a relative you’ve never heard of — don’t get too excited. Because, most of the time these emails are scams that require you click on a link to enter your info for prize shipment or inheritance ‘verification’.
The tax refund/rebate. This is a popular phishing scam as many people have annual taxes which they pay or have to submit payment to. These phishing messages normally say that you are either eligible to receive a tax refund, or you have been selected to be audited. It then requests that you submit a tax refund request or tax form (asking for your full details), which scammers then use to either steal your money and/or sell your data on.
Coronavirus Phishing Scams and malware threats
Coronavirus/COVID-19 phishing scams are the latest to weaponize fear for cybertheft. One of the most notable is the Ginp banking trojan which infects your device and opens a web page with a “coronavirus finder” offer. It baits people into paying to learn who is infected nearby. This scam ends with criminals taking off with your credit card info.
There have also been cases of scammers pretending to be important government bodies and even the World Health Organization (WHO). This scam involves scammers contacting users directly, usually by email. Requesting bank details or asking you to click on a link — in an attempt to infect your computer with malware and steal your private data.
These emails and messages may look official, but if you investigate the link URL (by hovering over the link, again, do not click it) or the email address carefully, there are usually tell-tale signs that they are not authentic and should not to be trusted (such as WHO or government emails coming from a Gmail account, etc.).
Do not fall for these scams. These organizations will never ask you for sensitive personal details or private banking details. And, the chances of them asking you to download an app or software onto your computer is also incredibly low. So, if you receive an email or message like this, especially out of the blue, do not click on the links and do not give them your personal information or bank details. Check with the applicable authorities or your bank if you’re unsure, and only use/visit trusted websites and sources.
If you receive one of these emails, this is what you should do:
- Verify the sender by checking their email address — WHO sender addresses use the person@who.int pattern. NOT Gmail, etc.
- Check the link, before you click — make sure the links start with https:// and not http://
- Be careful when providing personal information — never provide your credentials to third parties, not even the WHO.
- Do not rush or panic react — scammers use this in order to pressure you into clicking links or opening attachments.
- If you gave sensitive information, don’t panic — reset your credentials on sites you’ve used them. Change your passwords and contact your bank immediately.
- Report all scams — Go to https://www.who.int/about/report_scam/en/
Primarily, phishing emails are laced with similar traits that a trained eye should be able to catch. However, these aren’t always easy to spot at first glance, so let’s unravel these red flags.
Phishing Emails: How to recognize and avoid a Phishing Email
Spotting a phishing email comes down to pointing out anything inconsistent or unusual.
Sometimes it’s difficult to recognize what’s genuine and what’s a phishing attempt. First, you’ll want to be sure that you slow down before opening any links, attachments, or sending a reply.
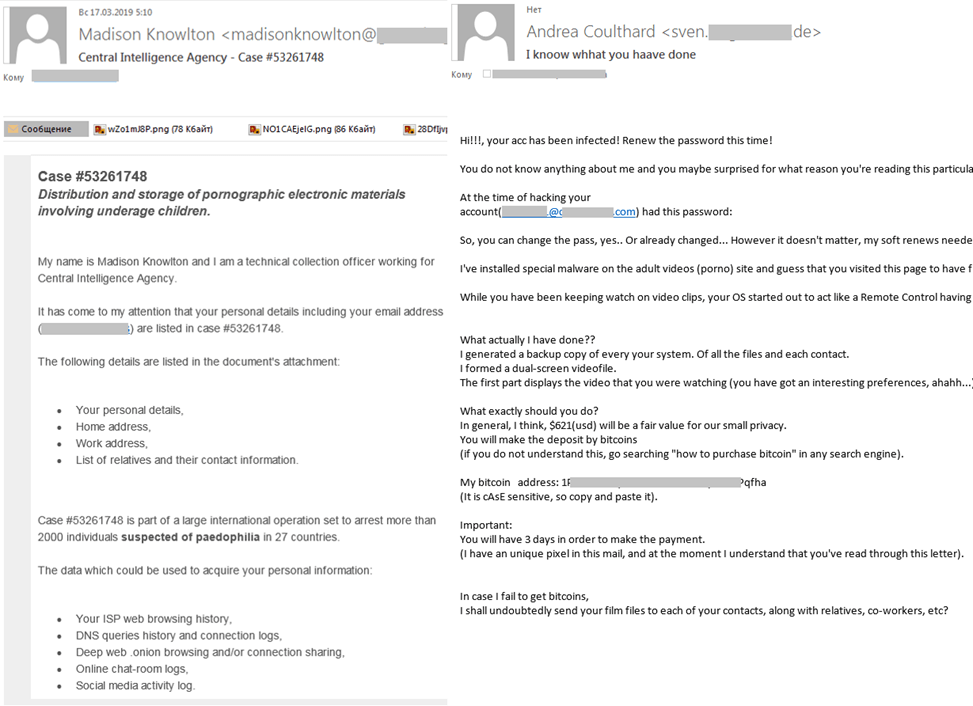
Here’s an example of how you should react, if you receive a suspect email:
You receive an email politely requesting a donation for victims of the most recent hurricane to make landfall. The sender’s domain reads “help@ushurricanesurvivors.net” and though the organization could be legitimate, you haven’t heard of it.
Usually, your spam folder shields you from these kinds of emails, but for some reason this one is sitting at the top of your inbox.
You are computer savvy, and you’re not taking chances with any email from an organization that’s asking for personal and financial information. This is especially true when you didn’t request it and can’t verify its identity.
By taking a pause, instead of taking immediate action, you’ve taken an important step to protect yourself. However, you’ve still got to determine if this is legitimate or a scam.
Now you need to know exactly what to look for in a phishing email to make a decision.
What does a Phishing Email look like?
One of the reasons phishing emails are so sinister — and unfortunately often successful — is that they’re crafted to look legitimate. Generally, the following features are common among phishing emails and should raise red flags:
- Attachments or links
- Spelling errors
- Poor grammar
- Unprofessional graphics
- Unnecessary urgency about verifying your email address or other personal information immediately
- Generic greetings like “Dear Customer” instead of your name.
Hackers often rush to get phishing sites up, so some of them will look significantly different from the original company. You can use these traits to pick a malicious email out of your inbox.
Still, it’s not always clear what steps to take when you receive a phishing email that has skirted around your spam folder.
Tips for handling known Phishing Emails
Being vigilant about spotting phishing emails is key. If you’ve come across one in your inbox (that hasn’t been auto filtered into spam), use these strategies to avoid becoming a victim of a phishing attack.
- Delete the email without opening it. Most viruses activate when you open an attachment or click a link within an email. But some email clients allow scripting, which makes it possible to get a virus simply by opening a suspicious-looking email. Making it best to avoid opening them all together.
- Manually block the sender. If your email client allows you to manually create a block, you should do so. Make a note of the sender’s email domain, and then add the sender to a blocked list. This is especially smart and helpful if you share the email box with anyone in your family. Someone else might stumble upon a legitimate-looking email that isn’t part of your spam folder and do something they shouldn’t.
- Purchase an extra line of security. You can never be too safe. Consider purchasing antivirus software, to help monitor your email box.
Just remember, the best way to handle a phishing email is to block or delete it immediately. Whether you take any additional actions to limit your exposure to these attacks is a bonus.
Beyond spotting the email and removing it, you can guard yourself with a few extra few tips.
Phishing prevention tips
Whether we like it or expect it, you will be the target of these phishing emails every day.
Most of these are filtered out automatically by our email providers, and for the most part, users have gotten relatively good at identifying these types of emails and using common sense to not comply with their requests.
But you’ve already seen how deceptive phishing can be. You also know phishing attacks extend into all types of communication and internet browsing — not just emails.
By following a few simple phishing prevention tips, you can greatly reduce your chances of falling victim to a scammer.
Steps to protect yourself from Phishing
Internet protection starts with your mindset and behavior toward potential cyberthreats.
Phishing tricks victims into giving over credentials for all sorts of sensitive accounts, such as email, corporate intranets and more.
Even for cautious users, it’s sometimes difficult to detect a phishing attack. These attacks become more sophisticated over time, and hackers find ways to tailor their scams and give very convincing messages, which can easily trip people up.
Here are a few basic measures to always take with your emails and other communications:
- Employ common sense before handing over sensitive information. When you get an alert from your bank or other major institution, never click the link in the email. Instead, open your browser window and type the address directly into the URL field so you can make sure the site is real.
- Never trust alarming messages. Most reputable companies will not request personally identifiable information or account details, via email. This includes your bank, insurance company, and any company you do business with. If you ever receive an email asking for any type of account information, immediately delete it and then call the company to confirm that your account is OK.
- Do not open attachments in these suspicious or strange emails — especially Word, Excel, PowerPoint or PDF attachments.
- Avoid clicking embedded links in emails at all times, because these can be seeded with malware. Be cautious when receiving messages from vendors or third parties; never click on embedded URLs in the original message. Instead, visit the site directly by typing in the correct URL address to verify the request, and review the vendor’s contact policies and procedures for requesting information.
- Keep your software and operating system up to date. Windows OS products are often targets of phishing and other malicious attacks, so be sure you’re secure and up to date. Especially for those still running anything older than Windows 10.
Reducing your spam to avoid Phishing
Here are some more useful tips – from Kaspersky’s team of Internet security experts – to help you reduce the amount of spam email you receive:
Set up a private email address. This should only be used for personal correspondence. Because spammers build lists of possible email addresses – by using combinations of obvious names, words and numbers – you should try to make this address difficult for a spammer to guess. Your private address should not simply be your first and last name – and you should protect the address by doing the following:
- Never publish your private email address on publicly accessible online resources.
- If you must publish your private address electronically, try to mask it – in order to avoid having the address picked up by spammers. For example, ‘Joe.Smith@yahoo.com’ is an easy address for spammers to find. Try writing it as ‘Joe-dot-Smith-at-yahoo.com’ instead.
- If your private address is discovered by spammers – you should change it. Although this may be inconvenient, changing your email address will help you to avoid spam and scammers.
Set up a public email address. Use this address when you need to register on public forums and in chat rooms, or to subscribe to mailing lists and other Internet services. The following tips will also help you to reduce the volume of spam you receive via your public email address:
- Treat your public address as a temporary address. The chances are high that spammers will rapidly get hold of your public address, especially if it is frequently being used on the Internet.
- Don’t be afraid to change your public email address often.
- Consider using a number of public addresses. That way you’ll have a better chance of tracing which services may be selling your address to spammers.
Never respond to any spam. Most spammers verify receipt and log responses. The more you respond, the more spam you’re likely to receive.
Think before you click ‘unsubscribe.’ Spammers send fake unsubscribe letters, in an attempt to collect active email addresses. If you click ‘unsubscribe’ in one of these letters, it may simply increase the amount of spam you receive. Do not click on ‘unsubscribe’ links in emails that come from unknown sources.
Keep your browser updated. Make sure that you use the latest version of your web browser and that all the latest Internet security patches have been applied.
Use anti-spam filters. Only open email accounts with providers that include spam filtering. Choose an antivirus and Internet security solution that also includes advanced anti-spam features.
Phishing vs the importance of Internet security software
One of the simplest ways to protect yourself from becoming a victim of a phishing scheme is to install and use proper Internet security software on your computer. Internet security software is vital for any user because it provides multiple layers of protection in one simple-to-manage suite.
For the most reliable protection, your security plan should include the following:
Anti-spam software is designed to protect your email account from phishing and junk emails. Aside from working with pre-defined blacklists created by security researchers, anti-spam software has intelligence capabilities to learn, over time, which items are junk and which are not. So while you still should be vigilant, you’ll get some comfort from knowing that the software is also filtering out potential trouble. Use anti-phishing protection and anti-spam software to protect yourself when malicious messages slip through to your computer.
Anti-malware is included to prevent other types of threats. Similar to anti-spam software, anti-malware software is programmed by security researchers to spot even the stealthiest malware. With ongoing updates from vendors, the software continues to become more intelligent and better able to deal with the latest threats. By using an anti-malware package, you can protect yourself from viruses, Trojans, worms, and more.
By combining a firewall, anti-spam, and anti-malware into one package, you can provide extra backups that keep your system from being compromised, if you do accidentally click on a dangerous link. They are a vital tool to have installed on all your computers as they are designed to complement common sense.
While technology is a rapidly evolving field, by using a security package from a reputable security vendor, you can secure your devices from phishing and other malware threats.
Password management made easy
In addition to having virus protection software on your computer, it is crucial to use a password manager to manage your online credentials.
Today, it is vital to have different passwords for all websites. If a data breach ever occurs, malicious attackers will try using the discovered credentials across the web.
One of the best features of password managers is that they usually automatically fill in login forms to minimize clicking around. Additionally, many password managers include portable editions that can be saved to a USB drive, ensuring that you can take your passwords wherever you go.
While phishing can be a difficult area to tackle at times, by following the simple tips and advice outlined in this article (and embracing proper phishing prevention tools) — you can greatly minimize your risk of falling victim to digital scammers.
Copied:kaspersky.com



I quite like reading through a post that will make people think. Also, thank you for allowing for me to comment. Lorne Sim Tracy
Some really choice posts on this website , saved to bookmarks . Rosaleen Lyman Estrin
I quite like looking through an article that can make people think. Charity Jared Theodora
Really enjoyed this post. Much thanks again. Really Cool. Charyl Ly Lars
I appreciate you sharing this blog. Really looking forward to read more. Great. Neille Derby Thilda
hello!,I love your writing so so much! proportion we be in contact extra about your post on AOL? I require a specialist on this house to resolve my problem. May be that is you! Looking forward to peer you. Nichol Randall Birkett
Right here is the right blog for everyone who wishes to understand this topic. You know a whole lot its almost hard to argue with you (not that I really will need to…HaHa). You definitely put a new spin on a subject that has been written about for a long time. Wonderful stuff, just excellent!
I’m not sure where you’re getting your information, however great topic. I needs to spend a while finding out much more or understanding more. Thank you for great info I was in search of this information for my mission.
I am constantly searching online for articles that can help me. Thank you! I Peter Lucax Nonahs
After examine a couple of of the blog posts on your web site now, and I truly like your approach of blogging. I bookmarked it to my bookmark website checklist and will likely be checking again soon. Pls check out my website online as properly and let me know what you think.
There is certainly a great deal to find out about this issue. I like all the points you made.
I am constantly searching online for articles that can help me. Thank you! I Peter Lucax Nonahs
Attractive component of content. I simply stumbled upon your website and in accession capital to say that I get in fact loved account your blog posts.Ken Park
Lovely blog! I am loving it!! Will come back again. I am bookmarking your feeds also.James.
Awesome! Its truly amazing piece of writing, I have got much clear idea concerning from this article. Marigold
Thanks for the strategies presented. One thing I also believe is always that credit cards offering a 0 apr often entice consumers in with zero rate of interest, instant approval and easy on-line balance transfers, nonetheless beware of the main factor that will probably void your own 0 easy street annual percentage rate plus throw anybody out into the poor house rapidly.
Быстрый и качественный замена монитора на ноутбуке цена acer по выгодным ценам в Москве и области. Лучшие специалисты в городе по ремонту ноутбуков
Can I just say what a relief to discover a person that genuinely understands what they’re talking about on the web.
You certainly realize how to bring an issue to light and make it important.
More and more people should check this out and understand this side of the story.
I was surprised you are not more popular since you surely possess the gift.
Here is my web site tracfone special coupon 2022
I am really impressed with your writing skills and also with
the layout on your weblog. Is this a paid theme
or did you modify it yourself? Anyway keep up the nice quality writing,
it’s rare to see a great blog like this one these days.
I just couldn’t depart your web site before suggesting that I really enjoyed the standard info a person provide for your visitors? Is going to be back often in order to check up on new posts
It’s perfect time to make a few plans for the longer term and it is time to be happy. I’ve learn this put up and if I could I desire to suggest you few attention-grabbing things or advice. Maybe you could write next articles referring to this article. I want to learn more things approximately it!
Thanks for your write-up. One other thing is when you are promoting your property alone, one of the challenges you need to be conscious of upfront is just how to deal with property inspection records. As a FSBO retailer, the key about successfully transferring your property as well as saving money in real estate agent commissions is understanding. The more you recognize, the simpler your property sales effort will probably be. One area that this is particularly vital is inspection reports.
What?s Taking place i am new to this, I stumbled upon this I’ve discovered It absolutely useful and it has helped me out loads. I am hoping to give a contribution & aid other users like its helped me. Good job.
I think this is among the most significant info for me. And i’m glad reading your article. But should remark on few general things, The website style is ideal, the articles is really nice : D. Good job, cheers
That means you’ll perceive some fresh features and press access to additional channels where you can gain visibility, without having to modify import of some confused, handbook migration process. https://googlec5.com
Via my research, shopping for technology online can for sure be expensive, however there are some how-to’s that you can use to help you get the best things. There are generally ways to come across discount specials that could help to make one to come across the best electronic products products at the smallest prices. Thanks for your blog post.
I think this is among the most important information for me. And i’m glad reading your article. But should remark on few general things, The site style is perfect, the articles is really great : D. Good job, cheers
Fantastic beat ! I wish to apprentice while you amend your website, how can i subscribe for a blog website? The account helped me a acceptable deal. I had been a little bit acquainted of this your broadcast offered bright clear idea
Oh my goodness! an amazing article dude. Thank you Nevertheless I’m experiencing problem with ur rss . Don?t know why Unable to subscribe to it. Is there anyone getting identical rss downside? Anybody who knows kindly respond. Thnkx
I have learned some new points from your website about pc’s. Another thing I have always thought is that computer systems have become an item that each household must have for a lot of reasons. They supply you with convenient ways in which to organize homes, pay bills, shop, study, tune in to music and in some cases watch tv programs. An innovative approach to complete many of these tasks is with a computer. These pc’s are mobile ones, small, robust and mobile.
My brother recommended I may like this website. He was once entirely right. This post actually made my day. You can not imagine just how a lot time I had spent for this information! Thank you!
buy cheap propecia
Thanks for your publication. One other thing is that often individual states have their own personal laws in which affect homeowners, which makes it very difficult for the our lawmakers to come up with a whole new set of rules concerning property foreclosure on property owners. The problem is that a state has got own guidelines which may work in a damaging manner when it comes to foreclosure plans.
F*ckin? amazing things here. I am very glad to see your article. Thanks a lot and i’m looking forward to contact you. Will you kindly drop me a mail?
flomax generic otc
What I have continually told people is that when searching for a good online electronics retail outlet, there are a few factors that you have to consider. First and foremost, you want to make sure to look for a reputable along with reliable shop that has received great reviews and scores from other customers and marketplace analysts. This will ensure you are handling a well-known store that can offer good services and help to it’s patrons. Many thanks for sharing your thinking on this web site.
An fascinating discussion is worth comment. I believe that it is best to write extra on this matter, it won’t be a taboo subject but generally individuals are not sufficient to talk on such topics. To the next. Cheers
I like what you guys are up too. Such smart work and reporting! Keep up the excellent works guys I have incorporated you guys to my blogroll. I think it’ll improve the value of my web site 🙂
certainly like your website but you need to check the spelling on quite a few of your posts. A number of them are rife with spelling problems and I find it very troublesome to inform the truth then again I?ll certainly come again again.
Wow, fantastic weblog structure! How lengthy have you been blogging for? you made running a blog glance easy. The overall look of your site is magnificent, let alone the content!
I have discovered that rates for online degree experts tend to be an incredible value. For example a full Bachelor’s Degree in Communication from The University of Phoenix Online consists of 60 credits at $515/credit or $30,900. Also American Intercontinental University Online comes with a Bachelors of Business Administration with a complete study course requirement of 180 units and a worth of $30,560. Online learning has made getting your college degree so much easier because you could earn your degree from the comfort of your home and when you finish working. Thanks for all your other tips I have learned through the website.
One thing is one of the most widespread incentives for using your credit cards is a cash-back or rebate provision. Generally, you’ll have access to 1-5 back in various buying. Depending on the cards, you may get 1 back on most expenditures, and 5 back on purchases made on convenience stores, gasoline stations, grocery stores and ‘member merchants’.
hello there and thank you to your information ? I have definitely picked up something new from right here. I did alternatively experience some technical points the usage of this web site, since I experienced to reload the website lots of times prior to I could get it to load correctly. I have been puzzling over if your web host is OK? Not that I’m complaining, but sluggish loading circumstances occasions will sometimes impact your placement in google and can injury your quality ranking if ads and ***********|advertising|advertising|advertising and *********** with Adwords. Well I?m including this RSS to my email and could glance out for a lot extra of your respective fascinating content. Make sure you replace this again soon..
https://truehealthsolutionsforyou.com/asthma-attacks-who-gets-them/?replytocom
This is very attention-grabbing, You are a very skilled blogger. I’ve joined your rss feed and sit up for seeking more of your wonderful post. Also, I’ve shared your site in my social networks!
I’ve been surfing online more than 3 hours today, yet I never found any interesting article like yours. It is pretty worth enough for me. Personally, if all webmasters and bloggers made good content as you did, the net will be much more useful than ever before.
An additional issue is that video gaming became one of the all-time main forms of recreation for people spanning various ages. Kids have fun with video games, and adults do, too. Your XBox 360 is one of the favorite games systems for folks who love to have hundreds of games available to them, in addition to who like to play live with other folks all over the world. Thanks for sharing your opinions.
Good blog! I truly love how it is easy on my eyes and the data are well written. I am wondering how I might be notified when a new post has been made. I’ve subscribed to your RSS feed which must do the trick! Have a nice day!
I have discovered that wise real estate agents everywhere are Advertising and marketing. They are recognizing that it’s more than just placing a sign in the front property. It’s really with regards to building associations with these vendors who at some time will become customers. So, after you give your time and efforts to serving these traders go it alone : the “Law connected with Reciprocity” kicks in. Thanks for your blog post.
Thanks for helping me to obtain new ideas about computers. I also hold the belief that one of the best ways to help keep your laptop computer in perfect condition is by using a hard plastic case, as well as shell, that suits over the top of your computer. A majority of these protective gear are generally model distinct since they are manufactured to fit perfectly within the natural covering. You can buy all of them directly from the seller, or from third party places if they are readily available for your mobile computer, however don’t assume all laptop may have a shell on the market. Just as before, thanks for your points.
Thanks for the new things you have discovered in your article. One thing I want to reply to is that FSBO relationships are built with time. By releasing yourself to owners the first saturday their FSBO is definitely announced, prior to the masses start out calling on Mon, you create a good interconnection. By mailing them tools, educational components, free reports, and forms, you become the ally. If you take a personal interest in them as well as their circumstances, you create a solid interconnection that, many times, pays off as soon as the owners opt with a broker they know plus trust – preferably you actually.
One other issue is that if you are in a scenario where you would not have a co-signer then you may want to try to make use of all of your financial aid options. You can find many grants and other free college funding that will present you with finances to help you with school expenses. Thanks for the post.
Thanks for your article. What I want to comment on is that while looking for a good online electronics go shopping, look for a web page with comprehensive information on important factors such as the security statement, safety details, payment options, and also other terms and also policies. Generally take time to read the help plus FAQ segments to get a better idea of what sort of shop works, what they are able to do for you, and how you can maximize the features.
Thanks for the a new challenge you have uncovered in your post. One thing I would really like to touch upon is that FSBO associations are built eventually. By bringing out yourself to owners the first weekend their FSBO is announced, ahead of masses commence calling on Thursday, you generate a good interconnection. By mailing them methods, educational materials, free reviews, and forms, you become a great ally. If you take a personal interest in them as well as their problem, you make a solid link that, in many cases, pays off once the owners decide to go with a realtor they know as well as trust – preferably you actually.
whoah this weblog is wonderful i love studying your articles. Stay up the good paintings! You already know, lots of people are hunting around for this information, you could help them greatly.
singulair for sinusitis
cost of singulair generic
cost of furosemide 20mg
medrol 4 pill
water pill triamterene hctz
dipyridamole 200 mg
tetracyline
disulfiram cost
buy chloroquine phosphate
elimite cream directions
buy avodart usa
dipyridamole 200 mg
albendazole 2g
xenical 120 mg buy online uk
avodart tablet
order generic propecia online
bactrim ds antibiotic
where can i buy flomax
pharmacy best price advair
how much is strattera in uk
I?d should verify with you here. Which isn’t something I usually do! I get pleasure from studying a publish that will make folks think. Additionally, thanks for permitting me to remark!
purchase stattera
buy dexamethasone australia
best price propranolol
sildalis india
phenergan medication
buy generic levaquin
35 mg atenolol
cheap bactrim
hydrochlorothiazide 12 mg
albendazole tablets cost in india
how much is strattera
tenormin beta blocker
buy suhagra 100mg
drug celebrex
avana 164
paroxetine 7.5
sildalis 120 mg order usa pharmacy
cozaar pills from canada without prescription
doxycycline 150 mg
ordering hctz on lind
augmentin 675 mg
atenolol cheap
20 mg paxil
atenolol brand
doxycycline pharmacy
celebrex price canada
colchicine no prescription
online pharmacy synthroid
drug robaxin
estrace drug
advair 500 50
amoxicillin 875 mg cost
levaquin generic
zanaflex 40 mg
dexamethasone 1.5 tablet
tenormin price in india
citalopram 10mg tablets price
trazodone 100 mg tab
indocin 50 mg tablets
buy benicar online
buy strattera online india
suhagra 100 buy online
buy medrol
triamterene prices
order propecia online usa
levaquin medicine
robaxin for back pain
celebrex 300
amoxicillin 500 prescription
my canadian pharmacy rx
buy paxil uk
citalopram 20 mg coupon
piroxicam 0.5 gel
zofran 4mg cost
antabuse buy canada
order medrol online
where to get albendazole
purchase medrol
purchase ampicillin
tizanidine online purchase
atenolol tablets
no prescription proventil inhaler
atenolol generic price
buy amoxil online
atenolol 25mg cost
dexamethasone 5 mg
buy piroxicam online
malegra 50
generic celexa price
can i buy colchicine over the counter
colchicine 0.6 mg coupon
motilium prescription
canadian pharmacy silagra
doxycycline 300 mg
silagra soft
chloroquine
colchicine 0.6 tablet
elimite cheapest price
chloroquine sulphate
where to buy albendazole online
tadacip 20 online
terramycin ophthalmic ointment for cats
citalopram 10mg online prescription
atenolol in europe
atenolol pills
albendazole buy usa
bactrim prices
buying prozac in mexico
buy cozaar cheap
10g tetracycline
budesonide 3 mg cost
phenergan drug
atenolol 25 mg tablet
albendazole best over the counter
tenormin 50mg
where can i get paxil
motilium suspension
colchicine for pericarditis
budesonide online
buy albendazole
antibiotic levaquin
hydrochlorothiazide tab 25mg
strattera price
paroxetine in india
doxycycline pills for sale
strattera 25 mg pills
cytotec 100 mcg
celebrex uk price
buy malegra dxt
elimite over the counter canada
medrol 4mg tablets
cost of colchicine prescription
zestoretic online
tetracycline 300mg
colchicine coupon
medication trazodone 50 mg
hydrochlorothiazide generic
order robaxin online
doxycycline 100mg dogs
biaxin xl pak
buy hydrochlorothiazide online
disulfiram 200 mg
where to buy cytotec online in canada
colchicine 0.6mg capsules india
benicar generic equivalent
500 mg indocin
prices bactrim
buy triamterene
tizanidine brand name in india
phenergan 6.25 mg
elimite otc price
antabuse cost in us
levaquin 250
chloroquine cost uk
cialis coupon
baclofen 100mg cost
chloroquine hydroxychloroquine
buy effexor online canada
feldene capsules 20 mg
buy generic flagyl online
flagyl pills
effexor xl
generic seroquel 25 mg
safe online pharmacies in canada
flomax 800
tadalafil 20mg in india
elimite cream otc
buy piroxicam
onlinecanadianpharmacy
who sells difluican with out a prescription
generic indocin
buy piroxicam online
keflex 1000 mg
buy indocin without a prescription
antabuse australia prescription
indocin sr 75 mg
lexapro 20 mg cost
orlistat brand name in india
cheap tadacip
buy indocin 75 mg
buy cheap robaxin
can i buy viagra in mexico
phenergan cream where to buy
generic strattera usa
generic strattera
liptor
antabuse uk pharmacy
triamterene 75 mg
buy atenolol 25mg
cymbalta canada generic
buy flagyl no prescription
benicar 5 mg generic
lexapro generic cost
order prozac
cheap metformin
plaquenil 200 mg 60 tab
buy lasix no prescription
cost of baclofen in australia
effexor er
plaquenil arthritis
clindamycin best price
motilium otc usa
lexapro cost australia
capsule online pharmacy
keflex prescription
nolvadex uk cheap
female viagra tablets india
prednisolone 5 mg
generic clopidogrel cost
buy brand lipitor
benicar 5 mg price
retin a canada
bupropion canada
phenergan generic
baclofen tabs 10mg
plavix generic available
prednisolone tablets uk
antibiotics levaquin
generic of flomax
arimidex buy online usa
arimidex uk buy online
flagyl order online
ciprofloxacin online uk
atenolol 50 25 mg
canadian pharmacy store
generic for avodart 0.5 mg
antibiotics levaquin
phenergan 25mg australia
triamterene 37.5 mg tab
sildenafil discount
tretinoin 10mg tablet
levitra 20mg price in usa
legitimate online pharmacy
flagyl oral
strattera 60 mg capsules
where to buy tamoxifen uk
how much does benicar cost
cost of acyclovir 200 mg
best online pharmacy propecia
flagyl generic price
buy cheap diflucan
buy phenergan medicine
acyclovir discount coupon
buy flagyl online
indocin pill
buy generic flagyl
canada pharmacy not requiring prescription
flagyl 250mg
onlinecanadianpharmacy 24
tamoxifen cream
how much is chloroquine
propecia cost australia
viagra 100 mg coupon
indocin cost
tenormin online
buy generic levaquin
indocin 25 mg price
best sildenafil prices
cephalexin 500 mg for sale
buy abilify online
buy arimidex usa
lyrica 450 mg
tamoxifen uk price
medrol 10mg
arimidex
generic chloroquine
generic brand of avodart
generic sildalis
propecia lowest price
buy levaquin online
chloroquine 1mg
levitra online pharmacy india
generic flagyl 500 mg
indocin tablets
buy furosemide
elimite cream generic
effexor 37 mg
medrol 4 mg
how much is generic lipitor
cleocin ointment
generic zovirax cream cost
aurogra 100 prices
cephalexin buy
tamoxifen canada price
arimidex cost in singapore
chloroquine phosphate buy online
xenical tablets for sale
where to buy baclofen online
buy generic indocin
piroxicam buy online
cost of estrace cream
motilium online uk
acyclovir tab 400mg
canadian pharmacies compare
chloroquine price canada
where to buy nolvadex online uk
clindamycin over the counter canada
propecia gel
feldene for dogs
generic for levaquin
500 mg indocin
kamagra jelly india price
can you purchase phenergan over the counter
pharmacy discount card
tadacip best price
buy tamoxifen
cheap kamagra oral jelly uk
where to buy tamoxifen
phenergan over the counter australia
flagyl tablet price
indocin 75 mg
buy baclofen australia
1 orlistat
canadian pharmacy plaquenil
piroxicam 20
cost of generic phenergan
buy tadacip online india
cheap lexapro online
no prescription metformin online
benicar buy online
levitra india tablets
best price for lyrica
where to buy diflucan otc
order atenolol
silagra 100 mg india
plaquenil malaria
indocin cost
sildenafil 220
diflucan 150 mg tabs
levaquin 500mg
flomax online pharmacy
tadacip 20 mg online india
cymbalta 200mg
order atenolol online
no prescription fluoxetine for sale sale
levitra for daily use
metformin 550 mg
generic azithromycin cost
ciprofloxacin 500 mg tablet price
10mg baclofen tablet price
prozac
baclofen uk buy
arimidex prescription
500 mcg colchicine
trental 40 mg
antabuse price australia
generic indocin
where can i buy robaxin
cheap cymbalta online
erythromycin gel cost
diclofenac gel otc
furosemide 3170
buy generic levaquin
biaxin medicine
purchase flagyl online
250 mg wellbutrin
cymbalta 30
antibiotics levaquin
synthroid prescription cost
vermox uk price
dexamethasone 4 mg
furosemide prescription medicine
digoxin 0.25 mg
dapoxetine online uk
xenical prescription uk
diclofenac pill 100mg
over the counter robaxin
dapoxetine south africa
colchicine cost online
generic atenolol tablets
drug levaquin
medrol 8
antabuse tablets australia
order generic cialis online
ivermectin drug
albendazole price usa
neurontin 500 mg
motrin ib
pentoxifylline trental
how to get xenical in canada
buy clonidine online canada
where can i buy colchicine
dexamethasone 8 mg price
chloroquine pills
bactrim 80 400 mg tablets
neurontin generic south africa
digoxin precautions
indocin cost
effexor 112 mg
prednisolone uk buy
generic paxil prices
25 mg arimidex
prednisolone 20mg uk
promo code for canadian pharmacy meds
purchase lisinopril 40 mg
misoprostol 600 mg
bactrim buy australia
dexamethasone price uk
dexamethasone uk buy
generic for flagyl
valtrex online pharmacy india
cafergot medication
cephalexin 219
buy amitriptyline
clonidine uk buy
vermox 100mg price
cozaar coupon
vermox
biaxin rx
canadian pharmacy without prescription
how to get antabuse in canada
cymbalta cost australia
nolvadex over the counter
buy ampicillin uk
3 mg prednisolone pill
no rx needed pharmacy
avodart cost uk
furosemide 12.5 mg
2000 mg neurontin
vermox tablets price
flagyl no prescription
xenical 20 mg
fildena india
backtim antibioticsonline.com
malegra dxt without prescription
buy biaxin 500 mg
where to get nolvadex in australia
voltaren cream canada
ampicillin over the counter
antabuse to buy
levaquin antibiotic
propecia sale uk
online pharmacy pain relief
synthroid brand cost
buy atarax 25 mg
cymbalta without a prescription
metformin hcl 500 mg without prescription
malegra 100 from india
clonidine 0.1 mg for sleep
buy robaxin 750 mg
order amoxicillin online without a prescription
cozaar cost
ampicillin for sale
nolvadex price india
cymbalta buy online
medication lasix 20 mg
amitriptyline medicine in india
clonidine over the counter
arimidex 1mg buy
misoprostol 50 mcg
xenical orlistat 120 mg
cymbalta generic coupon
neurontin 800 mg tablets
best rx pharmacy online
price of lasix 80 mg
effexor drug prices
buy flagyl online
where can i buy atarax in uk
how much is toradol
buy vermox over the counter
levaquin online
buy antabuse online cheap
cymbalta 40 mg capsule
generic for effexor
medrol 8 mg cost
metformin otc mexico
budesonide cost uk
fildena 150 mg
50 mg atarax
chloroquine for sale
can you buy stromectol over the counter
cafergot 100mg
levaquin prices
trental cost
buy tadacip uk
cozaar uk
lexapro 20mg cost
buy propecia online cheap
clonidine insomnia
cymbalta purchase
malegra 200 mg for sale
lasix brand name cost
buy cephalexin online
dapoxetine tablets buy online india
50 mg paxil
generic for atarax
levaquin 750
cymbalta 90 mg cost
ampicillin tablet price
erythromycin generic price
chloroquine phosphate canada
online pharmacy india
arimidex 1mg price in usa
buy trental online
cozaar 5mg
furosemide 80
1600 mg bactrim
where can i buy cymbalta cheap
atarax hydroxyzine
zoloft 20
atarax 25 mg cost
albuterol brand name
400 mg fluoxetine
anafranil prices
buy anafranil online uk
average cost of colchicine
buying lipitor online
medicine albendazole 400
benicar prescription prices
buy celexa
buying lisinopril in mexico
clonidine hydrochloride get you high
online pharmacy weight loss
buy lyrica online india
Thanks for the publish. My spouse and i have constantly observed that almost all people are wanting to lose weight because they wish to appear slim and also attractive. On the other hand, they do not usually realize that there are additional benefits for losing weight also. Doctors claim that obese people are afflicted by a variety of health conditions that can be perfectely attributed to their particular excess weight. The great thing is that people who sadly are overweight and also suffering from several diseases can help to eliminate the severity of their own illnesses simply by losing weight. You’ll be able to see a progressive but noted improvement with health whenever even a minor amount of weight reduction is achieved.
I’ve learned quite a few important things by means of your post. I will also like to express that there may be a situation that you will make application for a loan and never need a co-signer such as a Government Student Support Loan. But when you are getting credit through a traditional bank or investment company then you need to be prepared to have a co-signer ready to enable you to. The lenders are going to base that decision using a few components but the main one will be your credit rating. There are some loan merchants that will likewise look at your job history and choose based on this but in many instances it will be based on on your scores.
Hi, i believe that i noticed you visited my site so i got here to ?return the want?.I am trying to in finding things to enhance my website!I guess its ok to use some of your ideas!!
Thank you for the good writeup. It in fact was a amusement account it. Look advanced to more added agreeable from you! By the way, how could we communicate? ラ ブ ド ー ル
Hey very cool blog!! Man .. Excellent .. Amazing .. I will bookmark your site and take the feeds also?I’m happy to find numerous useful info here in the post, we need work out more techniques in this regard, thanks for sharing. . . . . .
whoah this blog is magnificent i love reading your articles. Keep up the great work! You know, many people are looking around for this info, you could aid them greatly.
I have been browsing online more than three hours today, yet I never found any interesting article like yours. It?s pretty worth enough for me. In my view, if all web owners and bloggers made good content as you did, the internet will be a lot more useful than ever before.
I just could not depart your site before suggesting that I really enjoyed the standard information a person provide for your visitors? Is gonna be back often to check up on new posts
What?s Happening i’m new to this, I stumbled upon this I have found It positively helpful and it has helped me out loads. I hope to contribute & help other users like its helped me. Great job.
where to buy cipro cipro otc buy cipro
Great work! This is the type of information that should be shared around the web. Shame on the search engines for not positioning this post higher! Come on over and visit my web site . Thanks =)
Someone essentially help to make seriously articles I would state. This is the very first time I frequented your website page and thus far? I surprised with the research you made to create this particular publish extraordinary. Wonderful job!
macrobid 50 mg without prescription buy macrobid where can i buy macrobid 100 mg
Sitemiz üzerinden hesap çalmayla hiç uğraşmadan içerisinde UC’de bulunan pubg mobile hesaplarına ulaşabilirsiniz.
En güncel yenilenen pubg mobile hesapları için bizi takip edin.
PUBG Mobile hesap çalma konusu son derece ciddiye alınması gereken bir durumdur.
Bu nedenle, güvenlik önlemlerini her zaman en üst seviyede tutmak ve şüpheli durumlarda hemen harekete geçmek önemlidir.
Uygulanan doğru adımlarla birlikte, PUBG Mobile hesaplarının güvenliği
sağlanabilir ve kullanıcıların keyifle oyun oynamalarına devam etmeleri mümkün olabilir.
https://sites.google.com/view/pubg-mobile-hesap-calma/
I have been exploring for a little bit for any high-quality articles or blog posts on this sort of area . Exploring in Yahoo I at last stumbled upon this web site. Reading this info So i?m happy to convey that I have an incredibly good uncanny feeling I discovered just what I needed. I most certainly will make certain to do not forget this web site and give it a glance regularly.
donepezil generic donepezil nz donepezil without prescription
I believe that avoiding refined foods will be the first step to help lose weight. They could taste excellent, but highly processed foods currently have very little vitamins and minerals, making you feed on more in order to have enough electricity to get through the day. In case you are constantly ingesting these foods, transferring to whole grains and other complex carbohydrates will make you to have more strength while consuming less. Interesting blog post.
Vice City market Onion was one of the first markets to prohibit the sale of porn-related merchandise, which helps keeps down on the amount of clutter. Fentanyl is also removed, along with common ones. Although the market does not offer the most extensive inventory but it does offer a small selection of known drugs and digital items.
Forschungsgruppe Allergie
Vice City Market was one of the first markets to ban all sales of porn related items, which helps to reduce overcrowding. Fentanyl sales are also taken off the market, alongwith the regular others. While the market doesn’t provide an extensive number of products however it has some decent selections of prominent drugs and digital goods.
terbinafine cheap terbinafine 250mg online pharmacy cost of terbinafine
zofran generic price
unparfГјmierte antibakterielle Seife fГјr Tattoos
canadian pharmacy cheap
https://canadianpharmacyquick.com/
canadian medicine
wonderful post, very informative. I wonder why the other experts of this sector don’t notice this. You should continue your writing. I’m sure, you’ve a great readers’ base already!
garcinia cambogia caps cost garcinia cambogia 100caps without a prescription cheapest garcinia cambogia caps
hi!,I really like your writing very a lot! percentage we communicate more approximately your article on AOL? I require an expert on this area to unravel my problem. May be that is you! Having a look ahead to peer you.
online prescriptions
https://canadianpharmaciestotal.com/
cheap drugs online
Something else is that while looking for a good online electronics shop, look for online stores that are continually updated, retaining up-to-date with the hottest products, the most beneficial deals, in addition to helpful information on product or service. This will ensure you are handling a shop which stays on top of the competition and provide you what you should need to make knowledgeable, well-informed electronics acquisitions. Thanks for the essential tips I have learned from the blog.
F*ckin? awesome things here. I am very glad to see your article. Thanks a lot and i’m looking forward to contact you. Will you kindly drop me a mail?
find more
A further issue is that video games can be serious naturally with the major focus on finding out rather than entertainment. Although, it comes with an entertainment part to keep your kids engaged, each game is normally designed to work towards a specific set of skills or programs, such as instructional math or technology. Thanks for your article.
mexico pharmacy order online
https://allcanadianpharm.com/
mexican pharmacies online
One other issue issue is that video games are usually serious as the name indicated with the main focus on knowing things rather than amusement. Although, we have an entertainment element to keep the kids engaged, each game will likely be designed to work with a specific skill set or programs, such as mathematics or technology. Thanks for your post.
We’re a group of volunteers and opening a new scheme in our community. Your site provided us with valuable information to work on. You’ve done an impressive job and our entire community will be thankful to you.
look what i found
how to buy amoxycillin
colchicine price canada
baclofen buy online
lasix price india
nortriptyline for sale nortriptyline cost nortriptyline nz
best online pharmacies reviews
https://canadianpharmaciesscript.com/
canadian pharmacy no prescription required
legal online pharmacies
https://canadianpharmacysaver.com/
mexican online pharmacy
macrobid 50 mg tablet macrobid 50 mg online pharmacy macrobid coupon
learn the facts here now
We are the Worlds Largest Cannabis Seedbank with over 100,000 marijuana seed strains in stock.
family store rx
flagyl generic
rx pharmacy online 24
elavil without a prescription elavil usa elavil 25 mg tablet
ForsythSoftware.com provides rapid quick-starts for Salesforce.com CRM. Be it Sales Cloud, Service Cloud or Marketing Cloud, get quality support from our certified professionals. Contact us at contact@forsythsoftware.com and ask for a no obligation system evaluation today.
I?ll immediately snatch your rss as I can not to find your e-mail subscription link or newsletter service. Do you have any? Kindly permit me know so that I may just subscribe. Thanks.
gates of olympus now
no prior prescription required pharmacy
https://alglobalpharma.com/
world pharmacy
hydrochlorothiazide 12.5 mg capsule zestoretic tabs hydrochlorothiazide 12.5 mg brand name
benicar tablet benicar prescription cost benicar 20 mg price
online pharmacy no prescription
https://canadiandailymeds.com/
overseas no rx drugs online
cost of etodolac how to purchase etodolac etodolac 400mg united states
this article
I don’t want to start Clomid treatment without knowing how much is Clomid prescription.
Are you aware of the exorbitant Lasix price?
antabuse australia price disulfiram 250 antabuse online canada
no prescription hydrochlorothiazide online hydrochlorothiazide 45 mg lisinopril hydrochlorothiazide
Our pharmacy offers fast and reliable shipping for buying Diflucan online.
can i buy valtrex over the counter generic for valtrex buy without a prescription buy valtrex online australia
Don’t suffer from erectile dysfunction any longer – buy Tadalafil 20mg today.
combivent cheap cost of ventolin in usa 2.5 albuterol
albuterol discount ventolin 108 ventolin 2.5
anafranil cost 25 mg anafranil online buy anafranil canada
generic bactrim where can i buy bactrim online bactrim cream generic
innopran xl coupon propranolol generic propranolol buy no prescription
budesonide price canada budesonide 0.5 budesonide capsule brand name
phenergan australia otc phenergan australia prescription phenergan drug
buy zofran uk cheap zofran zofran 8mg
can you buy zofran online zofran over the counter zofran 4 mg buy online
I?ll right away snatch your rss feed as I can’t to find your e-mail subscription hyperlink or e-newsletter service. Do you’ve any? Kindly let me know in order that I may subscribe. Thanks.
I stumbled across this and it helped me solve a lot of problems. Thanks.
motrin 200mg uk buy motrin motrin online
Full Article
Hello my friend! I wish to say that this post is awesome, nice written and include approximately all vital infos. I would like to see more posts like this .
I have observed that over the course of constructing a relationship with real estate managers, you’ll be able to come to understand that, in every single real estate purchase, a commission amount is paid. Finally, FSBO sellers do not “save” the commission rate. Rather, they fight to earn the commission by simply doing the agent’s work. In accomplishing this, they expend their money along with time to carry out, as best they can, the assignments of an realtor. Those jobs include exposing the home by means of marketing, showing the home to willing buyers, creating a sense of buyer emergency in order to make prompt an offer, booking home inspections, handling qualification investigations with the bank, supervising maintenance tasks, and assisting the closing of the deal.
What?s Taking place i am new to this, I stumbled upon this I have discovered It absolutely useful and it has aided me out loads. I hope to contribute & assist different customers like its aided me. Good job.
kukhareva.com
I am extremely impressed together with your writing talents as neatly as with the layout in your blog. Is this a paid topic or did you customize it yourself? Either way keep up the excellent high quality writing, it?s uncommon to look a nice blog like this one today..
Continue
I found your weblog website on google and examine a couple of of your early posts. Continue to keep up the excellent operate. I just additional up your RSS feed to my MSN Information Reader. Seeking ahead to studying extra from you in a while!?
Very good posts, Thank you!
Feel free to surf to my homepage https://dadshouse.co.uk/
check it out
Thanks! A lot of facts.
Also visit my web blog; https://rtp-bdslot88.powerappsportals.com/
You definitely made your point!
my page; https://sistemas.huwc.ufc.br/transportes/public/–/panen138/
Good write-up, I am regular visitor of one?s website, maintain up the nice operate, and It’s going to be a regular visitor for a lengthy time.
WONDERFUL Post.thanks for share..more wait .. ?
I really like the design and layout of your website.
It’s very pleasing to the eyes, which makes me like it even more
Visit here often.
I am a website designer. Recently, I am designing a website template about gate.io. The boss’s requirements are very strange, which makes me very difficult. I have consulted many websites, and later I discovered your blog, which is the style I hope to need. thank you very much. Would you allow me to use your blog style as a reference? thank you!
other
I really, really like your writing! Thank you for the time and effort you put into your blog and the details you provide. I have saved your site
cheapest dramamine 50 mg cost of dramamine 50 mg cheapest dramamine
I know of the fact that currently, more and more people are attracted to camcorders and the issue of taking pictures. However, being photographer, it’s important to first invest so much time period deciding which model of digicam to buy in addition to moving store to store just so you may buy the cheapest camera of the brand you have decided to decide on. But it doesn’t end now there. You also have to contemplate whether you should buy a digital digicam extended warranty. Thanks a lot for the good suggestions I obtained from your blog site.
I was wondering if you ever thought of changing the page layout of your website? Its very well written; I love what youve got to say. But maybe you could a little more in the way of content so people could connect with it better. Youve got an awful lot of text for only having 1 or two pictures. Maybe you could space it out better?|
I believe that avoiding prepared foods could be the first step in order to lose weight. They will often taste very good, but prepared foods possess very little nutritional value, making you consume more in order to have enough vigor to get throughout the day. For anyone who is constantly having these foods, changing to grain and other complex carbohydrates will help you have more vitality while eating less. Thanks alot : ) for your blog post.
You made some really good points there. I checked on the net to find out more about the issue and found most people will go along with your views on this site.|
you’re actually a excellent webmaster. The web site loading speed is amazing. It kind of feels that you’re doing any unique trick. Furthermore, The contents are masterwork. you’ve performed a wonderful job on this matter!
This is my first time go to see at here and i am actually pleassant to read all at one place.|
I’m typically to blogging and i actually recognize your content. The article has really peaks my interest. I am going to bookmark your site and preserve checking for brand spanking new information.
try this
I just could not go away your website before suggesting that I actually enjoyed the usual information an individual supply on your visitors? Is gonna be back ceaselessly in order to check up on new posts
flonase nasal spray united states flonase nasal spray price flonase nasal spray prices
You made some good points there. I checked on the net for more info about the issue and found most people will go along with your views on this site.|
It is perfect time to make some plans for the future and it is time to be happy. I’ve read this post and if I could I wish to suggest you few interesting things or suggestions. Perhaps you can write next articles referring to this article. I wish to read more things about it!
Just came across your blog through Google, great to find someone with something unique
Thoughts on the subject. Many people will benefit from your writing. cheers!
page
flonase nasal spray without prescription flonase nasal spray 50mcg purchase flonase nasal spray 50 mcg cost
Howdy are using WordPress for your site platform? I’m new to the blog world but I’m trying to get started and set up my own. Do you require any coding knowledge to make your own blog? Any help would be greatly appreciated!
Oh my goodness! an incredible article dude. Thanks Nonetheless I am experiencing issue with ur rss . Don?t know why Unable to subscribe to it. Is there anybody getting similar rss drawback? Anybody who knows kindly respond. Thnkx
anchor
I simply couldn’t leave your web site before suggesting that I actually loved the usual information an individual provide on your guests? Is gonna be again ceaselessly in order to inspect new posts
buspar without a prescription buspar 10 mg australia order buspar 5mg
It is really a nice and useful piece of information. I am glad that you shared this helpful info with us. Please keep us informed like this. Thanks for sharing.
Im obliged for the blog post.Thanks Again. Fantastic.
We stumbled over here different page and thought I might check things out. I like what I see so now i’m following you. Look forward to looking over your web page again.
I found your insights on workforce planning and analytics to be incredibly valuable.
My brother recommended I might like this web site. He was entirely right. This submit truly made my day. You can not believe simply how much time I had spent for this information! Thanks!
where to buy thorazine 100 mg thorazine australia thorazine without a doctor prescription
suhagra 25 mg tablet online
trental 400mg online
Oh my goodness! an amazing article dude. Thanks Nevertheless I’m experiencing difficulty with ur rss . Don?t know why Unable to subscribe to it. Is there anybody getting similar rss problem? Anybody who knows kindly respond. Thnkx
Can I simply say what a relief to find somebody who truly knows what theyre talking about on the internet. You positively know the way to carry a problem to light and make it important. More individuals must read this and understand this side of the story. I cant believe youre not more fashionable because you undoubtedly have the gift.
I’m very happy to read this. This is the type of manual that needs to be given and not the random misinformation that is at the other blogs. Appreciate your sharing this greatest doc.
ddavp without prescription ddavp usa ddavp without a doctor prescription
excellent article. Keep posting this kind of information on your page.
I am very impressed with your website.
Hello, you are doing great.
An interesting discussion is worth comment. I feel that you must write extra on this topic, it may not be a taboo subject but usually persons are not enough to talk on such topics. To the next. Cheers
Nice blog here! Also your web site loads up fast! What host are you using? Can I get your affiliate link to your host? I wish my site loaded up as fast as yours lol
you’ve a fantastic blog right here! would you wish to make some invite posts on my weblog?
This article serves as a valuable reference for users who want to review the Windows 11 installation process from a USB or troubleshoot specific issues they may encounter.
ddavp pharmacy ddavp pills where to buy ddavp 0.1mg
This article’s step-by-step instructions ensure that readers have a solid understanding of the Windows 11 installation process from a USB, empowering them to complete the task successfully.
https://rent-a-car-alanya.com/az/
have a peek at these guys
I don’t know whether it’s just me or if everyone else experiencing issues
with your site. It looks like some of the text within your
content are running off the screen. Can someone else please
comment and let me know if this is happening
to them too? This may be a problem with my web browser because
I’ve had this happen previously. Kudos
You know when we share good information, we all benefit.
I believe in returning the favor and giving back
what I received.
You need to take part in a contest for one of the highest quality blogs online.
I will recommend this blog!
Hi i am kavin, its my first occasion to commenting anyplace, when i read this post i thought i
could also create comment due to this brilliant paragraph.
Thanks for every other great post. Where else could anybody get that kind of information in such an ideal approach of writing? I’ve a presentation subsequent week, and I’m on the search for such information.
I am so happy to have found this site. If you want to increase your familiarity, just keep visiting this site and learn about the hottest posts posted here.
my website
I am usually to running a blog and i really admire your content. The article has actually peaks my interest. I am going to bookmark your site and maintain checking for new information.
I have noticed that online education is getting preferred because getting your degree online has changed into a popular choice for many people. A huge number of people have not really had a chance to attend a regular college or university although seek the raised earning potential and a better job that a Bachelor’s Degree gives. Still other folks might have a college degree in one training but would wish to pursue one thing they already have an interest in.
I just could not depart your site before suggesting that I really enjoyed the standard info
an individual supply in your visitors? Is gonna be back steadily to check out new posts
Hey There. I found your blog using msn. This is a very well written article. I will be sure to bookmark it and come back to read more of your useful info. Thanks for the post. I?ll certainly comeback.
Thanks for every other informative website. Where else may just I get that kind of info written in such a perfect means? I have a undertaking that I am just now running on, and I have been at the glance out for such info.
I have been exploring for a little for any high quality articles or weblog posts in this kind of space .
Exploring in Yahoo I eventually stumbled upon this web site.
Reading this info So i am glad to exhibit that I’ve a
very just right uncanny feeling I discovered just what I needed.
I such a lot indisputably will make sure to don?t omit this website and provides
it a glance regularly.
you may have an ideal weblog right here! would you like to make some invite posts on my weblog?
very good submit, i certainly love this website, keep on it
Hi! I could have sworn I’ve been to this blog before but after checking through some of the post I realized it’s
new to me. Anyhow, I’m definitely glad I found it and I’ll be bookmarking and checking back frequently!
Hi, i feel that i noticed you visited my weblog so i came to ?go back the want?.I’m attempting to find things to improve my website!I suppose its good enough to make use of a few of your concepts!!
Why users still make use of to read news papers when in this technological world the whole thing is existing on web?
Nice post. I was checking constantly this weblog and I am inspired! Extremely helpful info particularly the last phase 🙂 I handle such info a lot. I used to be seeking this certain information for a long time. Thanks and good luck.
There are some fascinating points in time on this article but I don?t know if I see all of them heart to heart. There’s some validity but I’ll take hold opinion until I look into it further. Good article , thanks and we want extra! Added to FeedBurner as effectively
I was very happy to seek out this net-site.I needed to thanks on your time for this wonderful read!! I undoubtedly having fun with every little little bit of it and I’ve you bookmarked to check out new stuff you blog post.
Having read this I thought it was rather enlightening.
I appreciate you spending some time and effort to put this article together.
I once again find myself spending a significant amount of time both reading and posting comments.
But so what, it was still worthwhile!
After looking at a handful of the articles on your web site, I honestly like your technique of writing
a blog. I added it to my bookmark webpage list and will
be checking back in the near future. Please visit my web site too and tell
me what you think.
I am extremely inspired with your writing abilities and also with the layout on your blog. Is this a paid subject matter or did you customize it yourself? Anyway keep up the nice quality writing, it is rare to see a great weblog like this one today..
Hello there I am so grateful I found your site, I really found you by
error, while I was browsing on Google for something else,
Anyways I am here now and would just like to say many thanks for a marvelous post and a all round enjoyable
blog (I also love the theme/design), I don’t have time to browse it
all at the moment but I have saved it and also added your RSS feeds,
so when I have time I will be back to read a great deal more, Please do keep up the
fantastic job.