Understanding the Need for Two-Factor Authentication
In a world where cyber threats are ever-present, relying solely on passwords can leave your accounts vulnerable. Two-Factor Authentication (2FA) adds an extra layer of security, requiring an additional piece of information or device to verify your identity. This guide aims to empower you with the knowledge and tools to implement 2FA effectively across various platforms.
What is 2FA?
Two-Factor Authentication (2FA) is a security process that requires two distinct forms of identification to access an account or system. It combines something you know (e.g., a password) with something you have (e.g., a mobile device or hardware token). This dual-layered approach significantly enhances security by ensuring that even if one factor is compromised, the account remains protected.
Types of 2FA
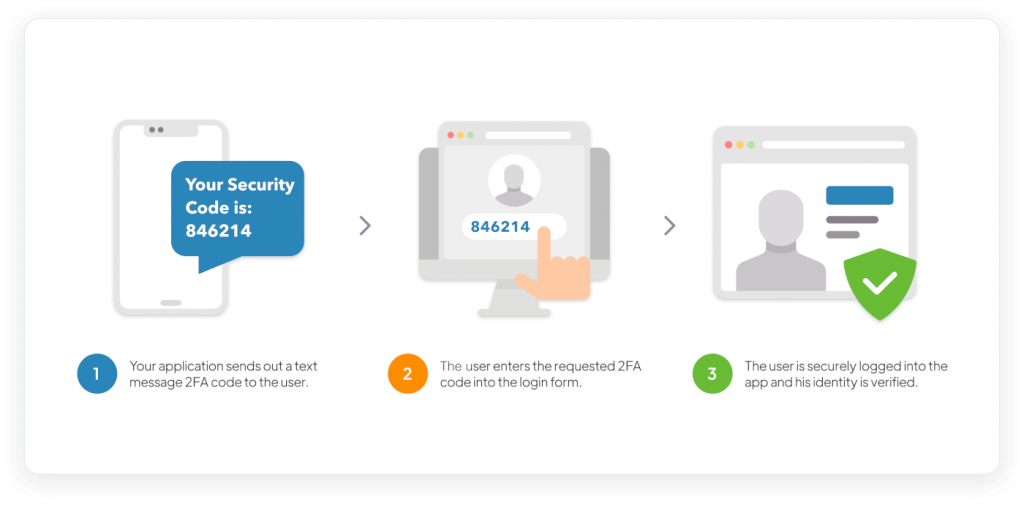
1. SMS-Based 2FA
SMS-based 2FA relies on sending a one-time code to your mobile device via SMS. This code serves as the second factor of authentication.
Step-by-Step Guide:
- Log in to your account.
- Navigate to the security settings.
- Enable SMS-based 2FA.
- Enter your mobile number.
- Receive and enter the verification code sent via SMS.
- 2FA is now active.
Best Practices and Security Considerations:
- Avoid Public Wi-Fi for 2FA: Using SMS-based 2FA on public Wi-Fi networks can expose you to risks. Use a cellular network or secure Wi-Fi instead.
- Sim Swap Attacks: Be cautious of SIM swapping attacks. Contact your mobile carrier to implement additional security measures.
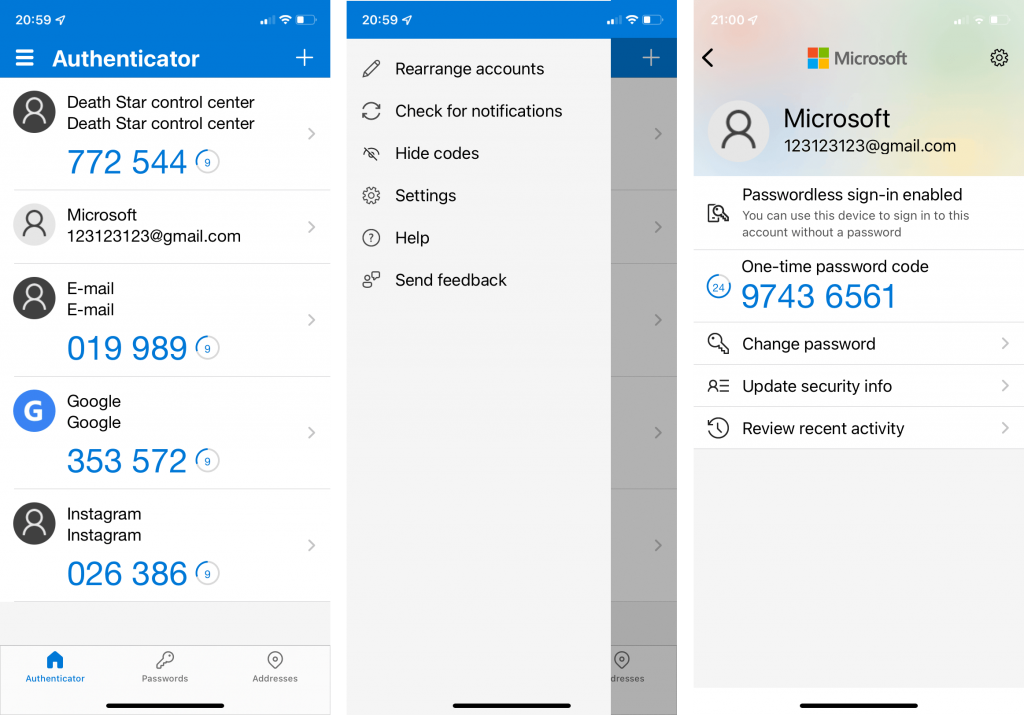
2. Authenticator Apps
Authenticator apps generate time-based one-time passwords (TOTPs) that change at regular intervals. They provide a more secure 2FA method compared to SMS.
Choosing the Right Authenticator App:
- Google Authenticator: A popular choice, especially for Google services.
- Authy: Offers multi-device support and encrypted backups.
- Microsoft Authenticator: Ideal for Microsoft ecosystem users.
Step-by-Step Setup Process:
- Download and install the chosen authenticator app.
- Log in to your account.
- Enable authenticator-based 2FA in your account settings.
- Scan the QR code displayed on your screen using the app.
- Enter the generated code to complete the setup.
Pros and Cons:
- Pros: Higher security level, no reliance on mobile network, support for multiple accounts.
- Cons: Can be more complex for some users, potential loss of access if the device is lost.
3. Hardware Tokens
Overview: Hardware tokens are physical devices that generate unique authentication codes. They offer a high level of security and are not reliant on a mobile device.
How Hardware Tokens Work:
- They utilize a cryptographic algorithm to generate time-based or event-based codes.
- The token is synchronized with the server, ensuring the generated code matches the server’s expectations.
Setting Up and Using Hardware Tokens:
- Acquire a hardware token compatible with your service provider.
- Log in to your account and navigate to security settings.
- Enable hardware token-based 2FA and follow the provided instructions for setup.
Ideal Use Cases:
- High-security environments, especially for critical infrastructure and sensitive data access.

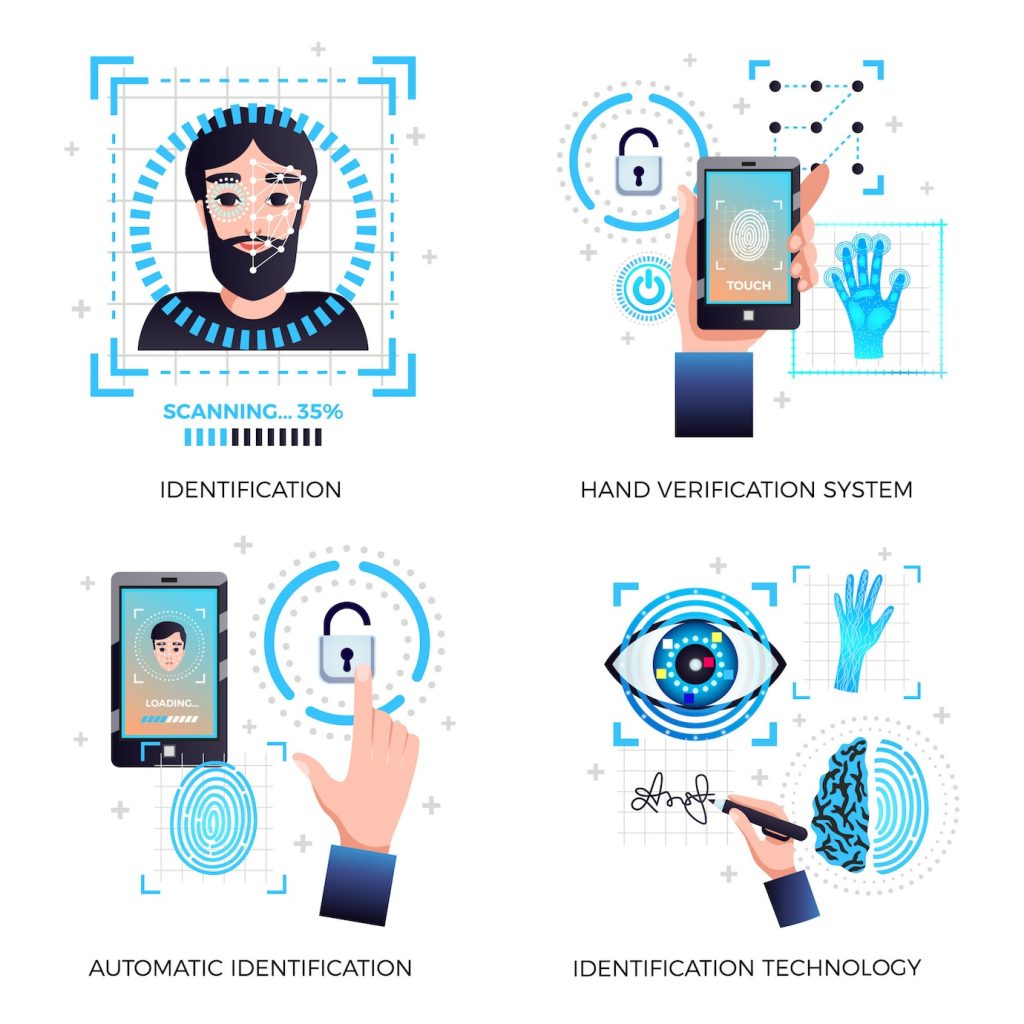
4. Biometric 2FA
Biometric 2FA leverages unique physical or behavioral characteristics for authentication. Common biometrics include fingerprints, facial recognition, and voice recognition.
Overview of Biometric Authentication:
- Biometric data is collected and converted into a digital format.
- This data is compared against stored biometric templates for authentication.
Implementing Biometric 2FA:
- Ensure your device has the necessary biometric sensors (e.g., fingerprint scanner, facial recognition camera).
- Enable biometric authentication in your account settings.
- Follow the prompts to enroll your biometric data.
Advantages and Limitations:
- Advantages: High level of security, convenient and user-friendly.
- Limitations: Reliance on specialized hardware, potential privacy concerns.
Backup and Recovery Options
What to Do When You Lose Access to Your 2FA Method
- Backup Codes:
- Many services provide backup codes during the initial setup of 2FA. These codes can be used in case you lose access to your primary 2FA method.
- Contact Support:
- Reach out to the support team of the service provider. They often have procedures in place to help users regain access.
Creating Backup Codes
- Locate and Save Backup Codes:
- During the initial setup of 2FA, the service provider may provide a set of backup codes. Locate and securely store these codes in a safe place.
- Use Backup Codes When Needed:
- In case you lose access to your primary 2FA method, log in to your account using one of the backup codes provided.
Recovery Process
- Recovery via Secondary Email:
- Some services allow you to recover access through a secondary email address linked to your account.
- Identity Verification:
- Be prepared to provide additional identity verification information to regain access to your account.
Managing 2FA for Multiple Accounts
Best Practices for Managing 2FA Across Various Platforms
- Consistent Methods:
- Whenever possible, use the same type of 2FA across different platforms to maintain a uniform level of security.
- Secure Storage:
- Store backup codes and recovery information in a secure location, preferably offline.
Streamlining the Process
- Use a Password Manager:
- Password managers like LastPass and 1Password can help you securely store and manage passwords and 2FA codes.
- Audit Your Accounts:
- Regularly review and update your 2FA settings, especially for critical accounts.
Common Issues and Troubleshooting
Addressing 2FA Setup Challenges
- Incorrectly Entered Codes:
- Double-check that you’re entering the correct code generated by your 2FA method.
- Time Synchronization Issues:
- Some authenticator apps rely on precise time synchronization. Ensure your device’s clock is accurate.
Troubleshooting Tips for Common Problems
- App-Specific Issues:
- Consult the help resources provided by the app or service you’re using for specific troubleshooting steps.
- Contact Support:
- If all else fails, reach out to the support team of the service for further assistance.
Security Best Practices Alongside 2FA
1. Password Hygiene
- Strong, Unique Passwords:
- Ensure your passwords are complex and not reused across multiple accounts.
- Password Changes:
- Regularly change your passwords to reduce the risk of unauthorized access.
- Avoiding Common Passwords:
- Steer clear of easily guessable passwords, such as “password” or “123456.”
2. Regular Security Audits
- Review Permissions:
- Periodically review the permissions granted to apps and services, revoking any unnecessary access.
- Check for Anomalies:
- Monitor your accounts for any unusual activities or logins.
3. Phishing Awareness
- Recognize Suspicious Emails:
- Be cautious of unsolicited emails asking for personal information or login credentials.
- Verify Links:
- Hover over links to see their destination before clicking, especially in emails.
2FA for Specific Platforms
Setting Up 2FA on Google
- Navigate to Security Settings:
- Go to your Google Account settings and select “Security.”
- Enable 2FA:
- Find the option for 2-Step Verification and follow the prompts to set it up.
2FA in Social Media: Facebook, Twitter, Instagram
- Facebook:
- Access your settings, navigate to Security and Login, and enable 2FA.
- Twitter:
- Go to your account settings, select Security and Privacy, and enable Login Verification.
- Instagram:
- In settings, select Security, then Two-Factor Authentication, and follow the prompts to enable.
2FA for Banking and Financial Accounts
- Contact Your Bank:
- Reach out to your bank to inquire about their specific 2FA setup process.
- Use Secure Banking Apps:
- Many banking apps offer their own 2FA methods for added security.
With this comprehensive guide, you now have a thorough understanding of how to set up and manage Two-Factor Authentication across various platforms and services. Remember, staying informed and proactive about cybersecurity is key to a safer online experience. Keep up with the latest developments in authentication methods to stay ahead of potential threats.
Start Setting Up Your 2FA Now!


